What is a Buffer Overflow Attack Types and Prevention Methods
By A Mystery Man Writer
Description
Attackers exploit buffer overflow issues to change execution paths, triggering responses that can damage the applications and exposes private information.

Exploit Development, Part 1: Anatomy of Buffer Overflows

Buffer Overflow Attack - ITperfection - Network Security

Buffer Overflow Attack - Cybersecurity Glossary

nmap cheet sheet 0.6.pdf - Nmap Cheat Sheet Scan Techniques Target Specification Switch -iL -iR -exclude Example nmap 192.168.1.1 nmap 192.168.1.1

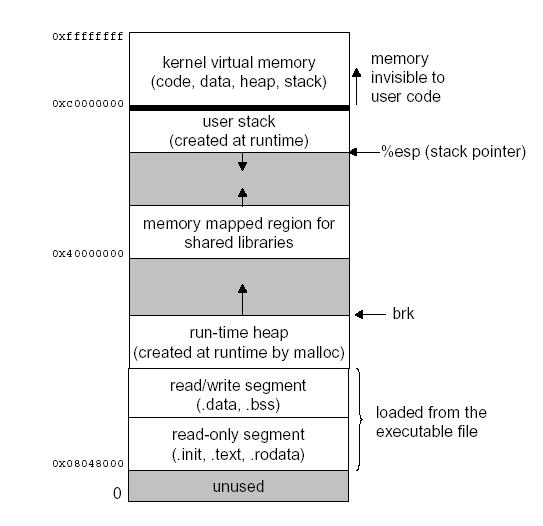
Buffer Overflow Attacks and Their Countermeasures

Buffer Overflow Attack Meaning, Types, and Prevention
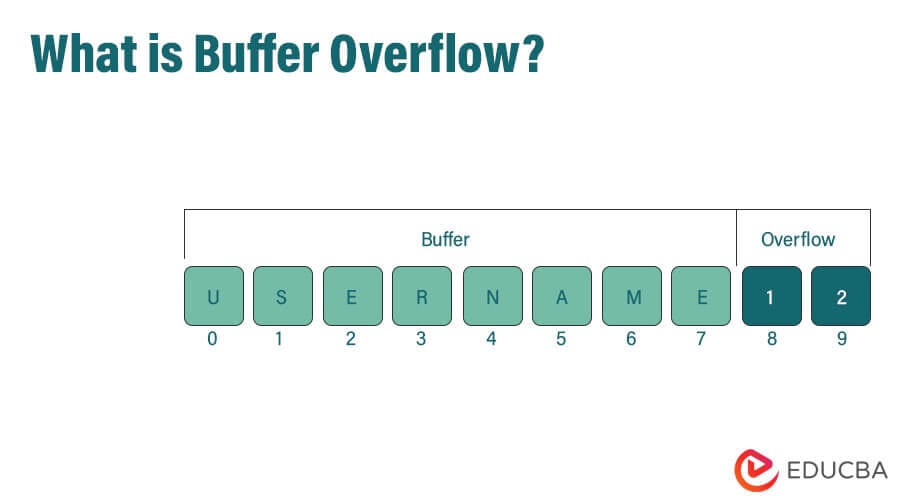
What is Buffer Overflow? Attacks, Solutions & Preventions

Lecture slides prepared for “Computer Security: Principles and Practice”, 3/e, by William Stallings and Lawrie Brown, Chapter 10 “Buffer Overflow”. - ppt download

nmap cheet sheet 0.6.pdf - Nmap Cheat Sheet Scan Techniques Target Specification Switch -iL -iR -exclude Example nmap 192.168.1.1 nmap 192.168.1.1
from
per adult (price varies by group size)